Contents
Cisco Router
Router with IOS 12.4 and below
tacacs-server host10.6.20.10 # this ip used as example tacacs-server keyTACACS_KEY aaa new-model aaa authentication logintacGUI group tacacs+ local aaa authentication enable default group tacacs+ enable aaa authorization exec default group tacacs+ local aaa authorization commands 0 default group tacacs+ local aaa authorization commands 15 default group tacacs+ local aaa accounting exec default start-stop group tacacs+ aaa accounting commands 0 default start-stop group tacacs+ aaa accounting commands 15 default start-stop group tacacs+ line vty 0 4 login authenticationtacGUI transport input ssh
Router with IOS 15.x and higher
tacacs servertacGui address ipv410.6.20.10 # this ip used as example keyTACACS_KEY aaa new-model aaa authentication logintacGUI group tacacs+ local aaa authentication enable default group tacacs+ enable aaa authorization exec default group tacacs+ local aaa authorization commands 0 default group tacacs+ local aaa authorization commands 15 default group tacacs+ local aaa accounting exec default start-stop group tacacs+ aaa accounting commands 0 default start-stop group tacacs+ aaa accounting commands 15 default start-stop group tacacs+ line vty 0 4 login authenticationtacGUI transport input ssh
Cisco Switch
Switch with IOS 12.4 and below
tacacs-server host10.6.20.10 # this ip used as example tacacs-server directed-request tacacs-server keyTACACS_KEY aaa new-model aaa authentication logintacGUI group tacacs+ local aaa authentication enable default group tacacs+ enable aaa authorization exec default group tacacs+ local aaa authorization commands 0 default group tacacs+ local aaa authorization commands 15 default group tacacs+ local aaa accounting exec default start-stop group tacacs+ aaa accounting commands 0 default start-stop group tacacs+ aaa accounting commands 15 default start-stop group tacacs+ line vty 0 4 login authenticationtacGUI transport input ssh
Searching for example!
Do you have an example? Share instruction with us, please - developer@tacacsgui.com.
Cisco ASA and Tacacs
Cisco ASA and Tacacs configuration
aaa-servertplus protocol tacacs+# set the aaa-server name aaa-servertplus (netmgmt ) host10.6.20.10 # set the interface and ip address for the defined above aaa-server keyPSK # set the password aaa authentication serial console LOCAL# auth for the serial console, better set as local aaa authentication ssh consoletplus LOCAL aaa authentication enable consoletplus LOCAL aaa accounting commandtplus
Cisco Nexus (NX-OS) and Tacacs
Cisco Nexus (NX-OS) and Tacacs configuration
feature tacacs+ ip tacacs source-interface loopback 0 tacacs-server host10.6.20.10 keyPSK aaa group server tacacs+tplus server10.6.20.10 aaa authentication login console local aaa authentication login default grouptplus local aaa authorization config-commands default grouptplus local aaa authorization commands default grouptplus local
Also be ware that you have checked this parameter for Tacacs User – Clone the login password. You can find it on tab Extra Options inside the user settings.
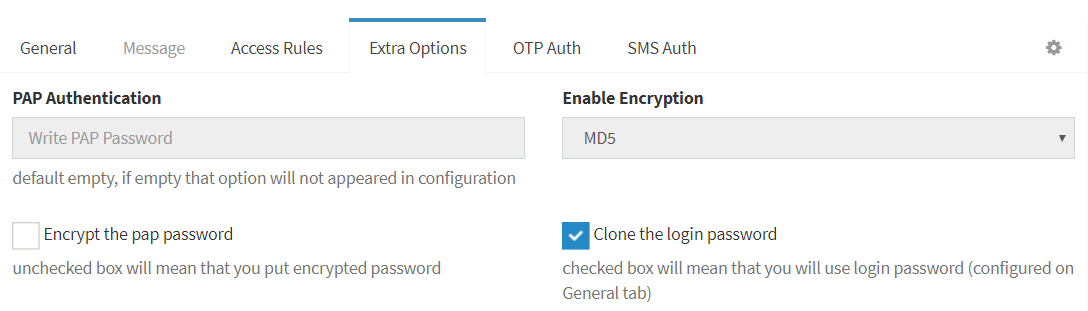
If checked user will have additional parameter pap, it clones the parameter login. In the configuration it will look like:
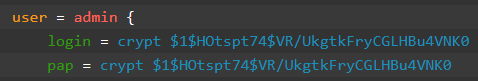
for local user
OR
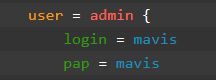
if user uses MAVIS module (like OTP or SMS)
Cisco WLC and Tacacs
Cisco WLC and Tacacs configuration
config tacacs auth add 110.6.20.10 49 asciiTACACS_KEY config tacacs auth add 210.6.20.10 49 asciiTACACS_KEY config tacacs athr add 110.6.20.10 49 asciiTACACS_KEY config tacacs athr add 210.6.20.10 49 asciiTACACS_KEY config tacacs aссt add 110.6.20.10 49 asciiTACACS_KEY config tacacs aссt add 210.6.20.10 asciiTACACS_KEY config aaa auth mgmt tacacs local
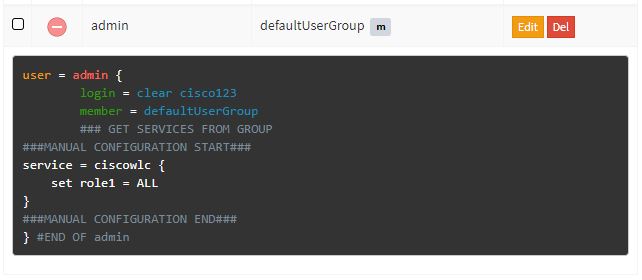
Also you have to add this service to user (you can do that manually):
service = ciscowlc {
set role1 = ALL
}
User should looks like this:
Created at: 2018-05-05 00:11:15
Updated at: 2018-10-10 17:47:45
Author: Aleksey Mochalin
Updated at: 2018-10-10 17:47:45
Author: Aleksey Mochalin