MAVIS LDAP. OpenLDAP Server configuration
Brief Plan
Create OpenLDAP user for the ldap connection
Tacacsgui configuration example
Test Connection to OpenLDAP server
Test Authentication
Create OpenLDAP user for the ldap connection
In this example I use phpLdapAdmin to see and change OpenLDAP scheme. Below you can see the user that will be used for connection. We need to know two main attributes – dn (distinguishedName) and password.
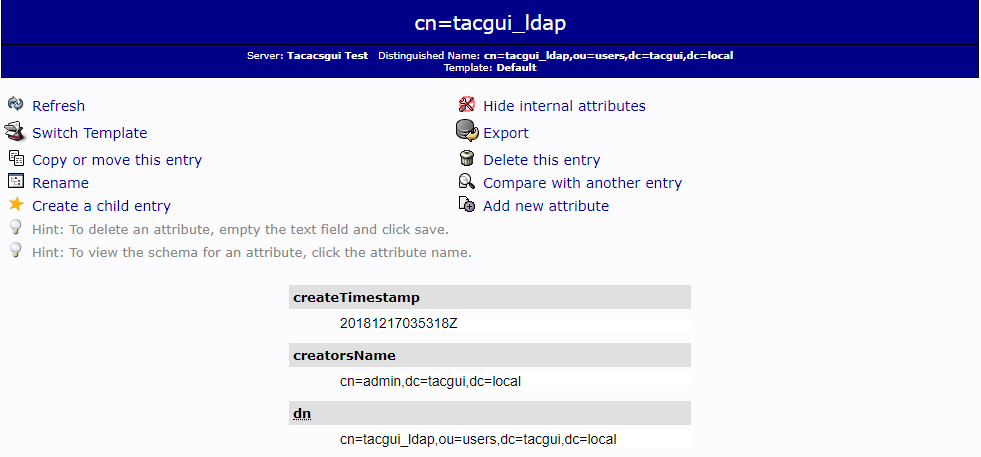
User for LDAP communication
Tacacsgui configuration example
As you can see we use distinguishedName as a parameter for user name. It is important for connection. Also you can see that this example use attribute uid to authenticate users.
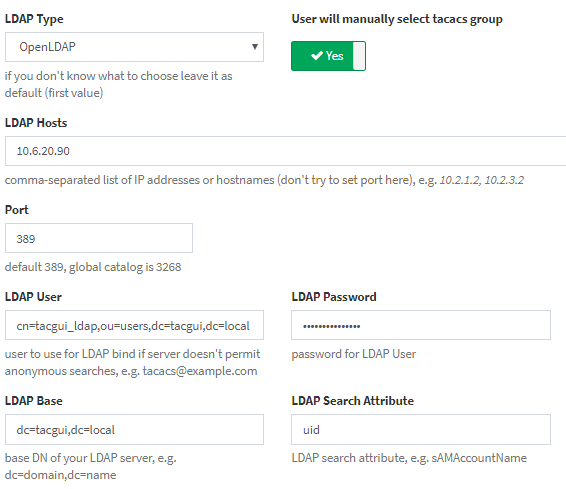
Tacacsgui configuration example
Test Connection to ldap server
In the example below we use the same user that we used for ldap connection. The RESULT NAK is ok, because user does not match any tacacs group.
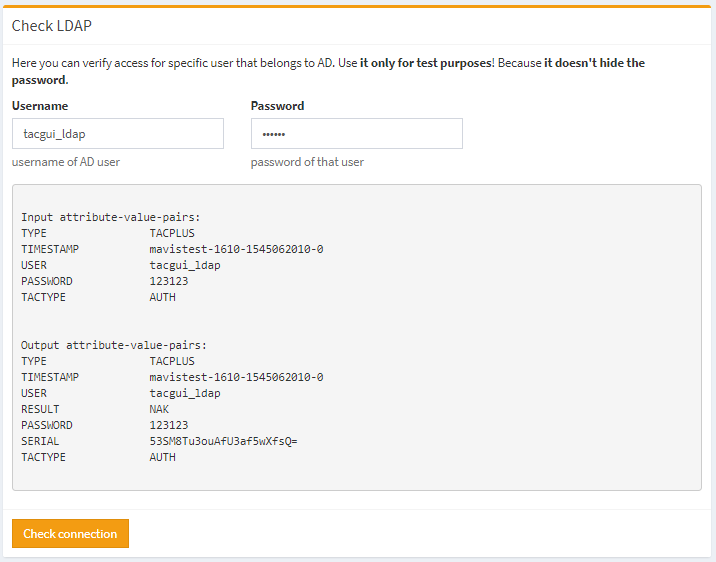
Test Connection
Test Authentication
Configure Tacacs user group!
Add a Tacacs user group. The group must have the same name as one of OpenLDAP group (CN) that user belong or OpenLDAP group must be added inside of tacacs user group. How to add Tacacs User Group?Try to authenticate OpenLDAP user.
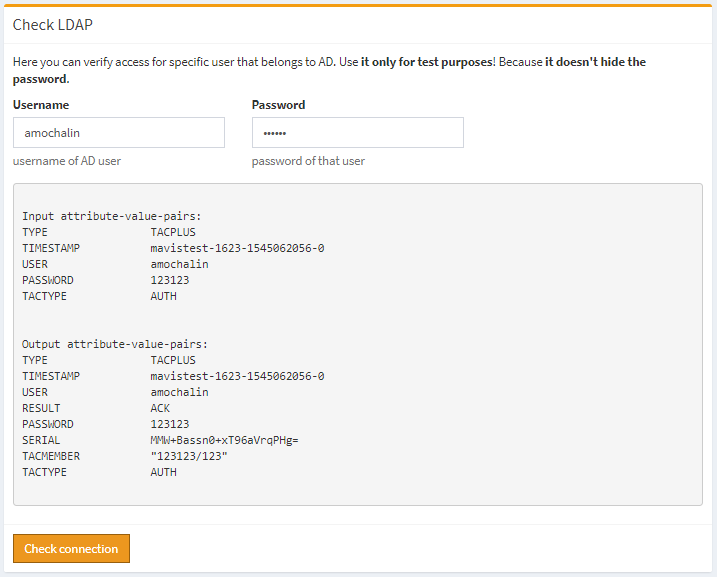
OpenLDAP
As you can see test authentication process return success message – RESULT ACK. Also that output show for us that user can be the member of two groups – 123123 and 123 (default group will be 123123, because it is the first in the list TACMEMBER “123123/123”.
If you see RESULT ACK, it is the good time to check your configuration on real devices.

